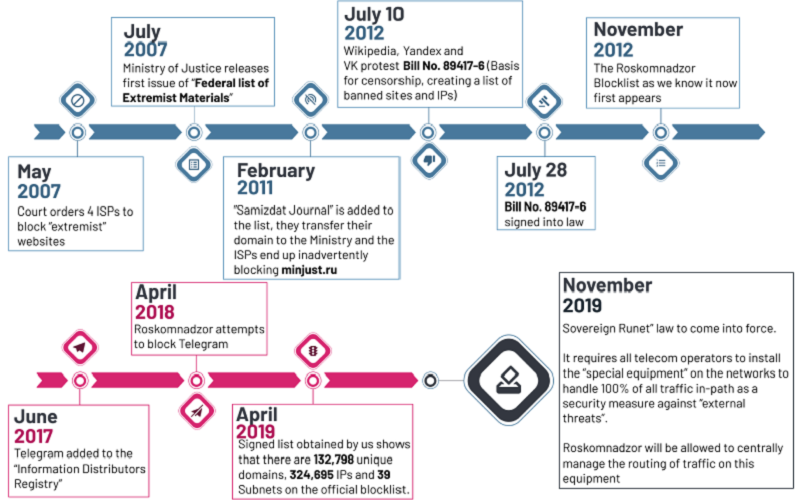
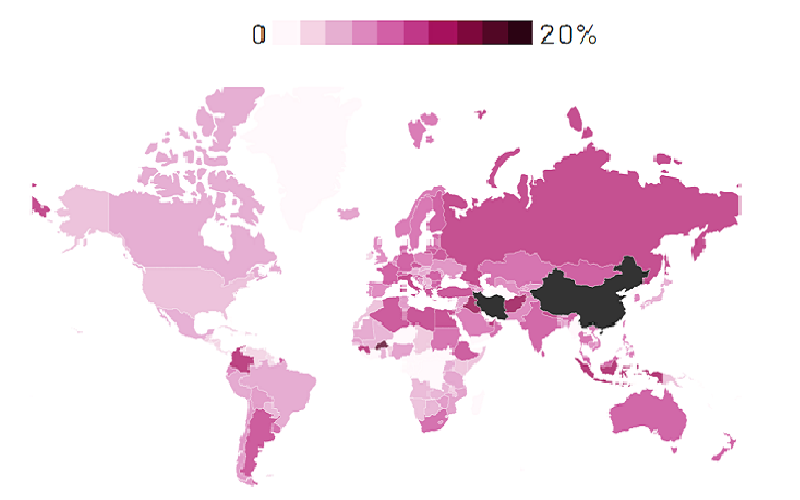
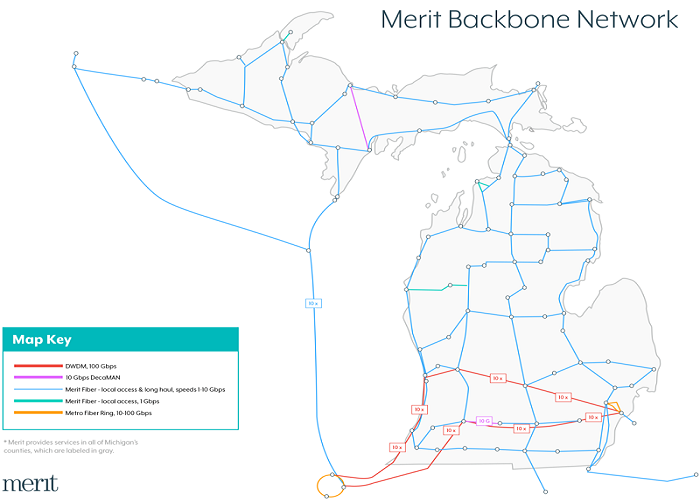
I’m a software engineer working on point-of-sale systems at Square (Block, Inc). I received my Master’s in computer science from Princeton University on a full scholarship (PhD candidacy) and received my Bachelor’s in computer science magna cum laude from the University of Michigan.
Before software engineering, my focus was on academic research in the fields of computer networks, security, and privacy. I’m very thankful to have worked with amazing mentors in this space: Dr. Michalis Kallitsis, Prof. Roya Ensafi, Prof. Jennifer Rexford, Prof. Jonathan Mayer, and at Nokia Deepfield. I also really enjoy teaching and have taught about six semesters of Data Structures & Algorithms (EECS 183, COS 226).